Autopsy 4.19.0 with Hosts, Analysis Results, and OS Accounts
By Brian Carrier
Autopsy 4,19.0 is out! We got a bit off from our quarterly release cycle in the past year and this release has code that started 9-months ago. So there’s a lot in here and therefore this release blog post is a bit longer than usual.
We’re happy to announce that we’ve aligned Autopsy with our Cyber Triage tool so that they use the same database, so many of the features that came into Autopsy were with the help of that team (also at Basis Technology).
You can download the latest version here.
This blog summarizes the following new features:
- Organizing data sources by hosts and persons.
- Data Artifacts vs Analysis Results
- Associating files and artifacts with OS Accounts
- Performance improvements
There’s a lot more too, which you can see here in the release notes.
Hosts and Persons
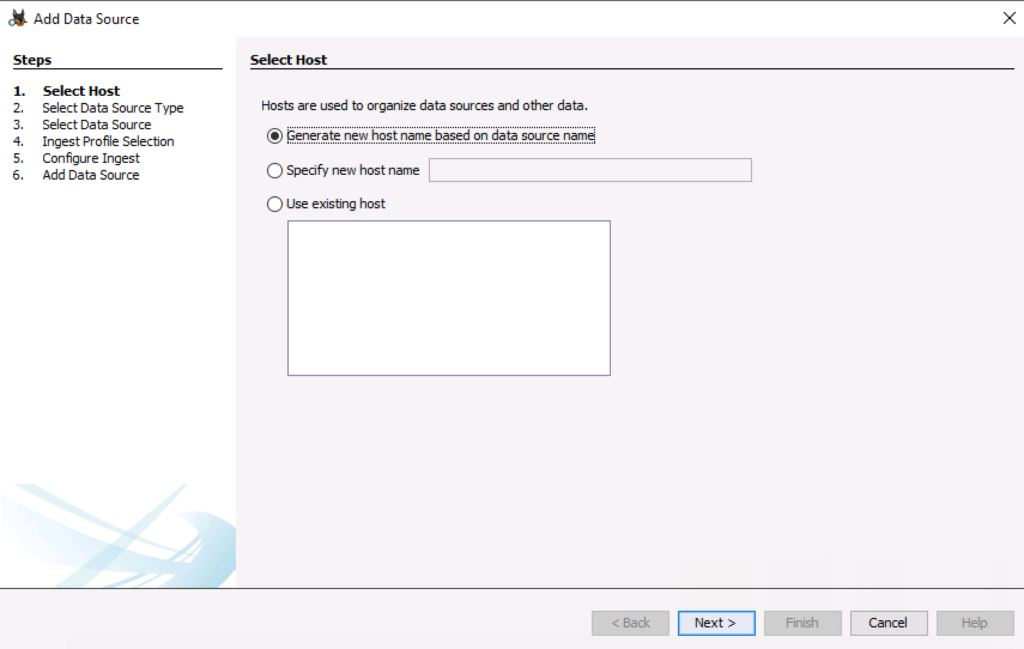
The first thing you’ll notice when you make a new case in the new version is that it is going to prompt you to specify the host the data source is from. A default one will be selected if you don’t want to specify it.
The main concept is that each data source is part of a host (or phone, device, etc.) and you can group them together. For example, if a host has multiple drives, then they can be grouped to make them easier to find in a big case.
Next, you can optionally add hosts and associate them with a Person. This allows you to put a name, such as “John Doe” to a phone, computer, and media card. The main idea is to allow you to more easily organize the data sources in your case instead of relying only on the data source name.
Data Artifacts and Analysis Results
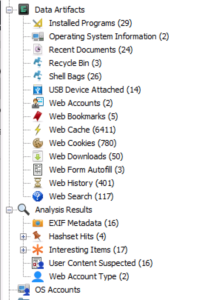
Another thing you may notice next is that the tree has slightly changed and there is another “Analysis Results” viewer in the lower right. Autopsy 4.19.0 separated the concepts of “Analysis Results” and “Data Artifacts”, which were previously stored in the same way as “Blackboard Artifacts”.
- A Data Artifact is data extracted from some other file or artifact. For example, a Web History artifact from a SQLite database.
- An Analysis Result stores the conclusions from some kind of analysis technique, such as searching a file for keywords or hash values.
Autopsy could always store these kinds of data, but they were not separated.
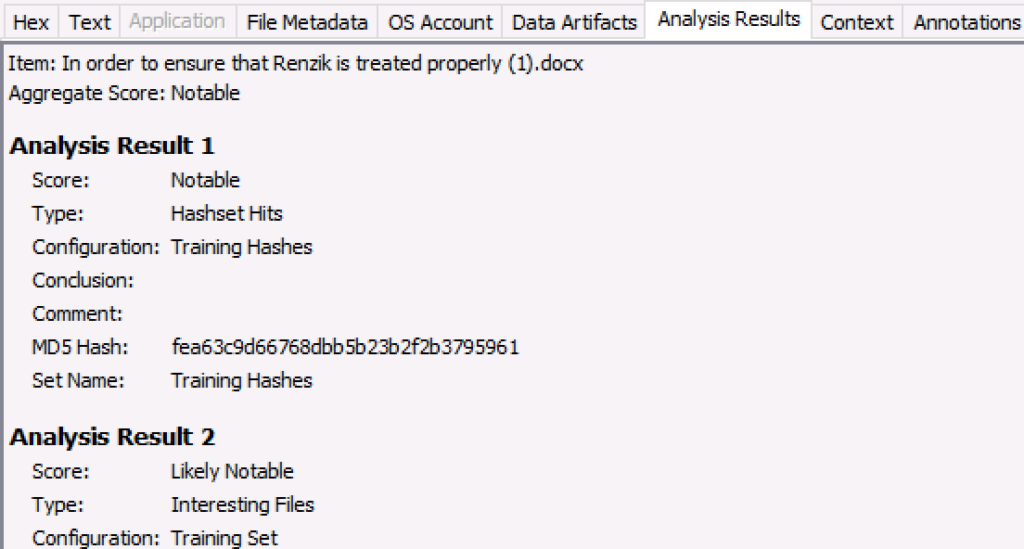
The separation occurred because Analysis Results can now include a score to show how relevant it is to the investigation. Cyber Triage needed the scoring because its modules vote on how likely an artifact is to be associated with an intrusion. We’ll talk more about that later.
There are two main impacts that you’ll see in the newest version. First, the tree now has sections for Data Artifacts and another for Analysis Results. Look in the Data Artifacts section for things extracted from other things. Look in the Analysis Results section for outputs of analysis techniques.
Lastly, we used to always have a “Results” viewer in the lower right that had both of these types of data. Now, there is a new Analysis Results viewer that lists the results that a given item has (such as its keyword hits or Yara hits).
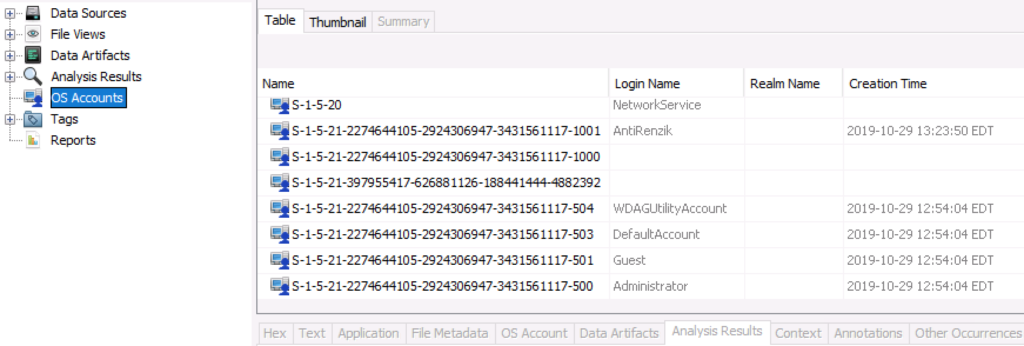
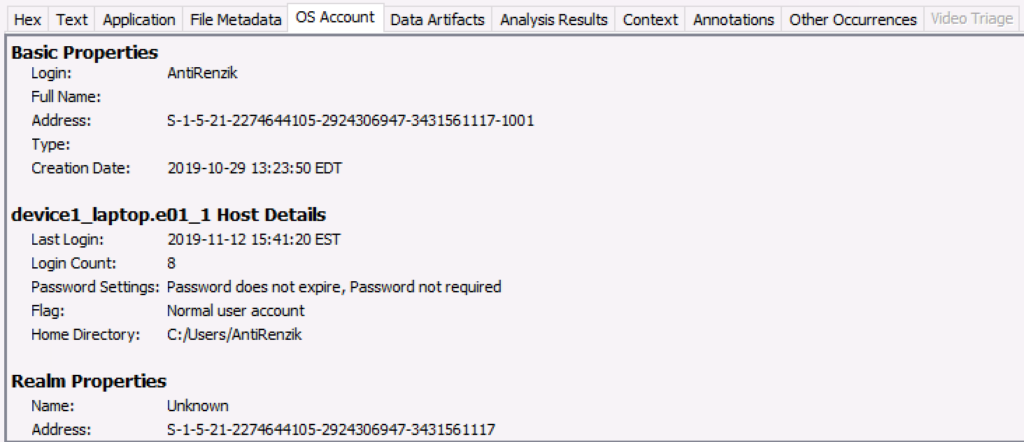
Operating System Accounts
Another Cyber Triage-motived feature is that Operating System Accounts are now “First Class Citizens”. They were previously stored as the more generic “Blackboard Artifacts” and not linked with any activity of that user. Now, files and data artifacts can be associated with a user.
Cyber Triage needed this feature in the database so that examiners can easily determine what processes, artifacts, and logins were associated with a given account. This makes it easier to look for account take over.
Autopsy’s use of the data is not quite yet as robust, but you can now see all of the OS Accounts in the tree.
And you can see which account is associated with a selected item.
You can learn more about them here.
Performance Improvements
We also spent a lot of time looking at bottlenecks and fixing those to give performance improvements in various places. The details are not relevant for this level of blog, but here are some examples:
- Recent Activity was made faster by using more efficient file searches and not committing the Solr index for each RegRipper report.
- Language ID is performed only on a small chunk of a file instead of all of the text.
- Embedded file extractor module has been made faster by doing file typing in memory and adding extracted files in batches.
- Various UI panels do more DB queries on background threads.
Get It Today
You can download the latest version and try out these new features from here.
Cyber Triage 3.0 will be out in a couple of weeks with the new database, but you can try version 2 from here in the mean time.