Autopsy 4.7 Includes Link Analysis, Database Viewers, Triage, and More
Blog
14 May 2018
With the latest Autopsy release, you have access to many new features and fixes. This post will give a high-level overview of the notable ones.
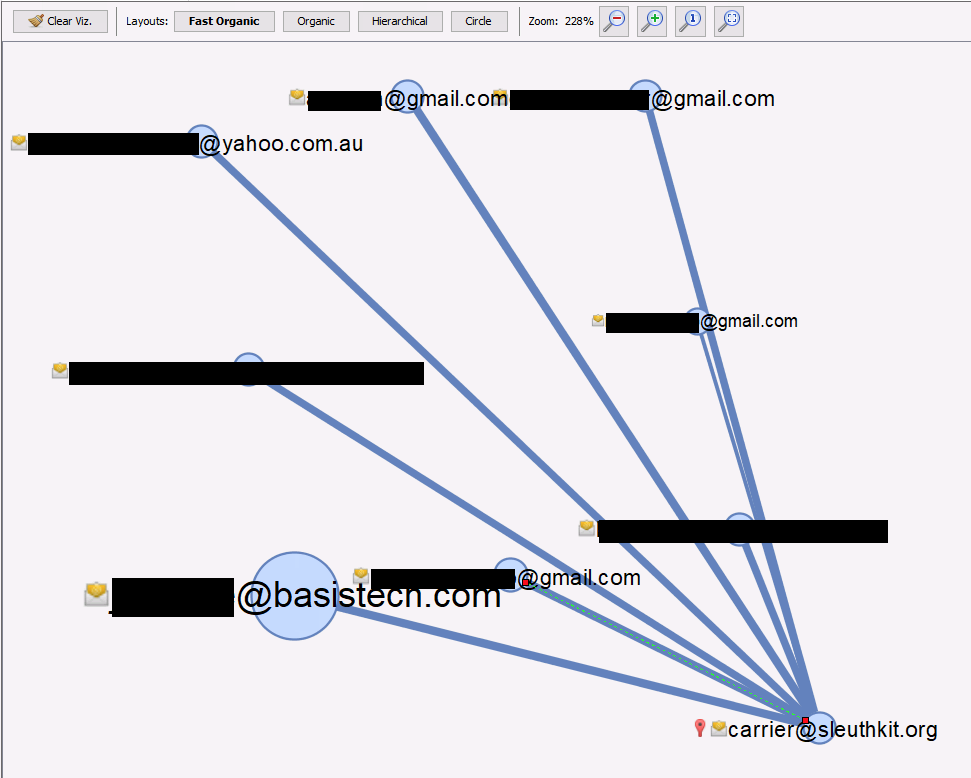
- Communications: The previous 4.6.0 release included a new Communications visualization as part of our work with DHS S&T. The overall goal of this effort is to improve Autopsy’s ability to store and display email and social media communications. This release continues that effort with a new link analysis UI to show connections between accounts. To make the UI less overwhelming, you need to add an account to the visualization by right-clicking on it in the table view and “Pinning” it. From there, you can see what accounts it communicated with. We’ll do a more in-depth blog posting about this in the coming weeks.
- Linux and OS X: This release is the first official one to support Linux and OS X out of the box. The basic gist at this point is to install a package of The Sleuth Kit 4.6.1 Java via either our .deb Linux package or brew (with special arguments) on OS X, install Java, run a script in the Autopsy ZIP file to put things in the right place, and it should work. Full details are in the Running_Linux_OSX.txt file.
- Application Viewer with SQLite and PList: The list of content viewer modules in the lower right was getting long, so we merged some together into a new “Application” content viewer that focuses on displaying files based on their type. This viewer will show pictures and movies (the functionality from the previous “Media” tab) and now allows you to navigate SQLite databases and binary plists.
- Triage Recent Files: Ingest filters allow you to limit what files go down the ingest pipelines and are useful for triage situations when you want to analyze only a subset of files. Previous versions allowed you to filter based on name and folder. Now you can also filter based on dates and send files down the pipeline only if they were modified or created within a certain number of days.
- Open Password Protected ZIP files: Autopsy has always flagged password protected ZIP files, but it was up to you extract the file, supply a password, and add the extracted files back in as “local files”. Now, you can right-click on a ZIP file, supply the password, and Autopsy will extract the files and add them back into the Case.
- Volatility: In the “Experimental” module in Autopsy, you can now ingest a memory image and Volatility will run on it. The Volatility output will be added as files and some files will be parsed to look for file paths. If the file paths are found in disk images in the current case, they will be flagged. We’ll migrate this into the core Autopsy release once the features are a bit more general. To enable “Experimental”, go to Plugins under the Tools menu, choose the Installed tab, and “Activate” the Experimental module.
The full list of changes can be found here.
Download the latest version from here.