Autopsy and Log4J Vulnerability
This post outlines Autopsy and the associated Log4J vulnerability released in Dec 2021 and outlined in CVE 2021-44228.
The last several Autopsy releases (the most recent was 4.19.2 on Nov 11) have shipped with two versions of log4j.
- Autopsy itself uses version 1.2
- Apache Solr embeds 2.13.2
The version Solr embeds has the vulnerability. Note that we have not done any review to determine if it is possible for user data to be logged.
See below for mitigation techniques based on the type of Autopsy deployment and type of case you are opening.
For more information, refer to the Solr page on this issue. Thanks to Ann Priestman for her testing of these fixes.
Dec 22 Update: Autopsy 4.19.3 was released with the fixed version of Log4J. Autopsy continues to use Log4J v1 and we will be looking into upgrading that in the next major release.
Single User Case
When you open a single user case in Autopsy, the embedded version of Solr is used. To disable the vulnerable feature:
- Close Autopsy.
- Open the following file in a text editor:
- C:\Program Files\Autopsy-4.19.2\autopsy\solr\bin\autopsy-solr.in.cmd
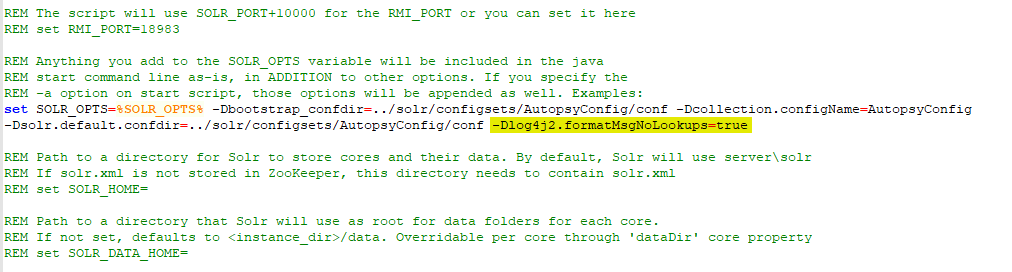
- Go to line 81 where you’ll see a line that starts with “set SOLR_OPTS=”. Append the following to the end: “-Dlog4j2.formatMsgNoLookups=true”. So, it should look like:
- To confirm it worked, open Autopsy and open a case.
- Open a web browser on the same system and point it at:
- http://localhost:23232/solr/#/
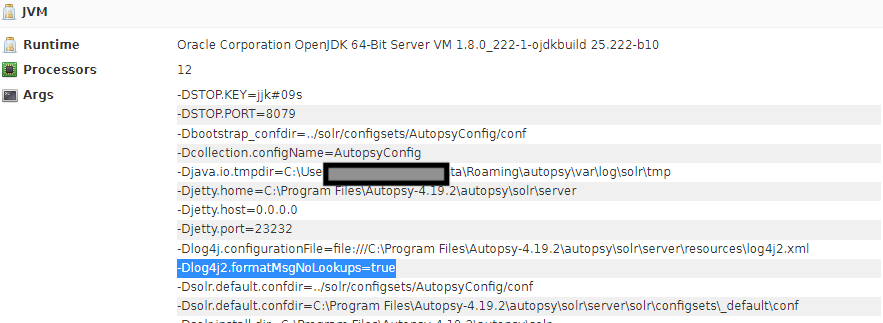
- Confirm you can see the above log4j configuration.
Multi-User Case
In a multi-user cluster, you need to configure and install your own version of Solr. We recommend you upgrade to 8.11.1 once it is available. In the mean time, you can use one of the techniques outlined in the Solr page The easiest fix at this point is to edit the solr.in.cmd file and edit the line to disable the lookups.
set SOLR_OPTS=%SOLR_OPTS% -Dlog4j2.formatMsgNoLookups=true
New Release
After this initial posting, Autopsy 4.19.3 was released with the updated version of the log4j libraries.