Autopsy 4.22.0: BitLocker Support, Cyber Triage Sidecar, Library Updates
Autopsy 4.22.0 is available!
Big features for this release are BitLocker support, ability to run alongside Cyber Triage, and updates to lower-level libraries.
You can download the release here and get the full release notes here.
You can download an evaluation copy of Cyber Triage here.
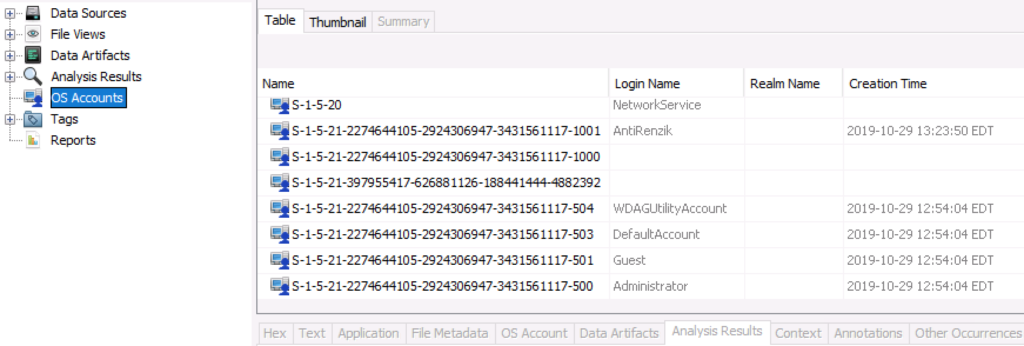
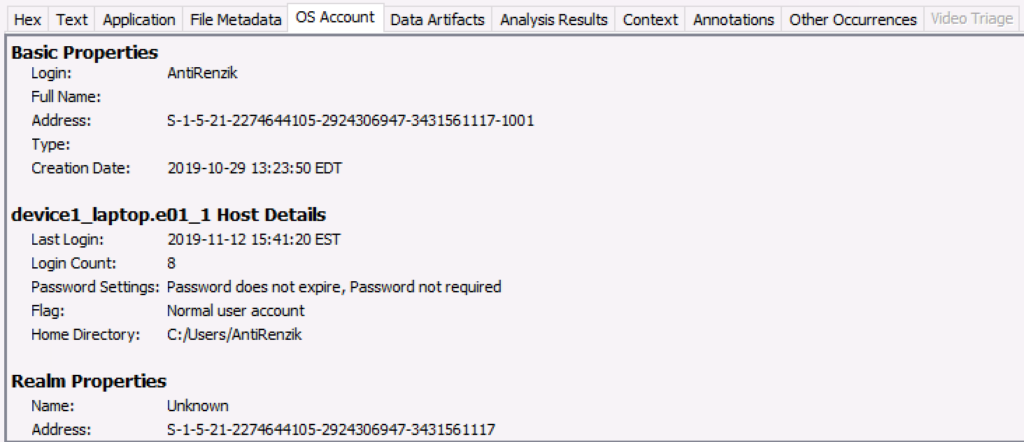
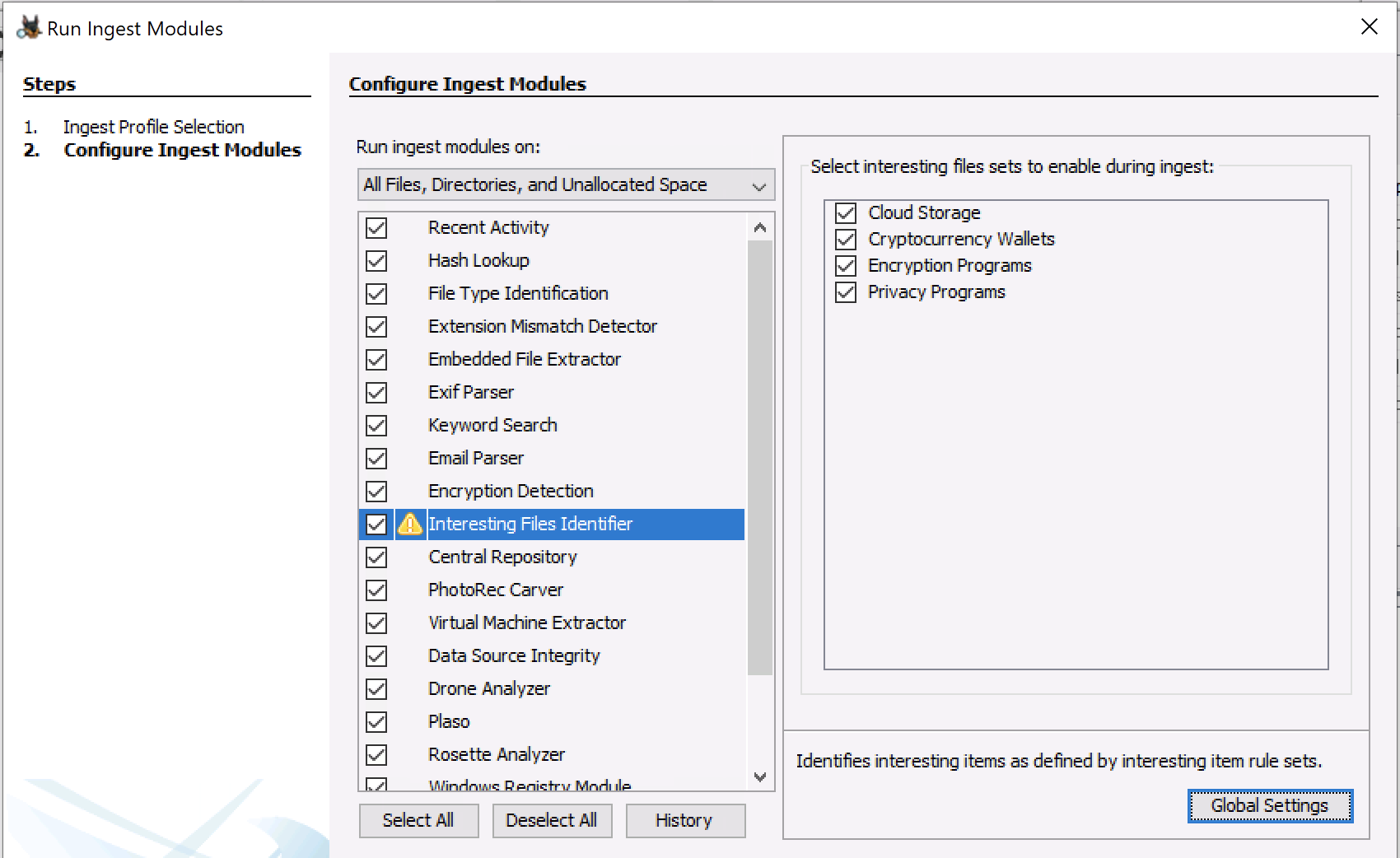
BitLocker Support
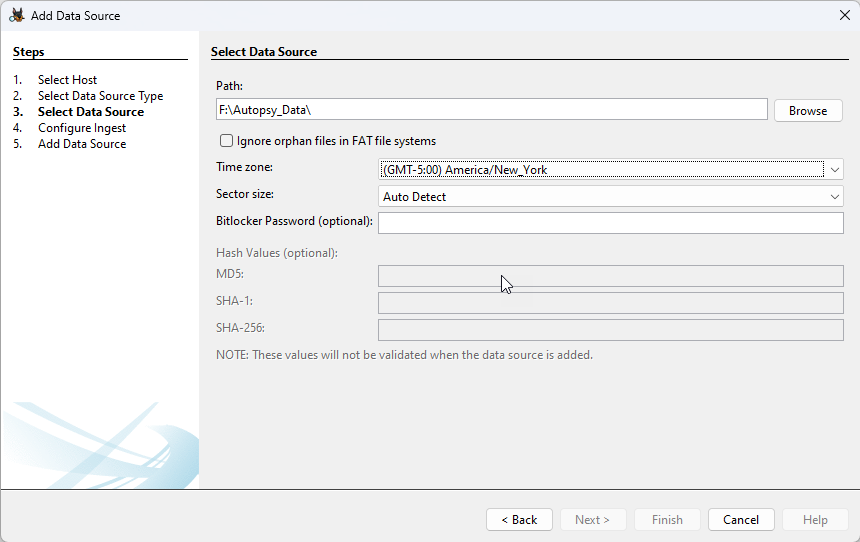
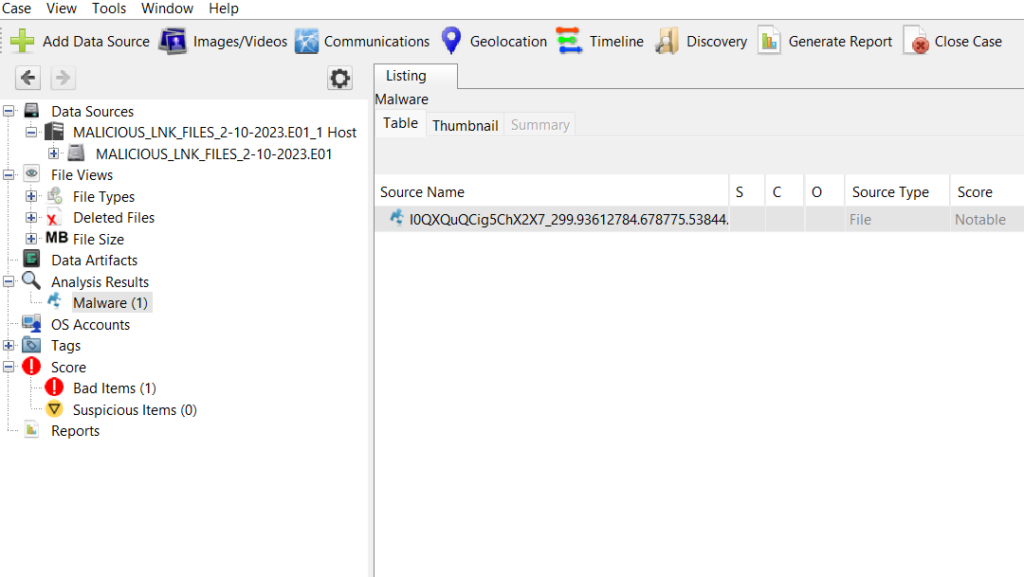
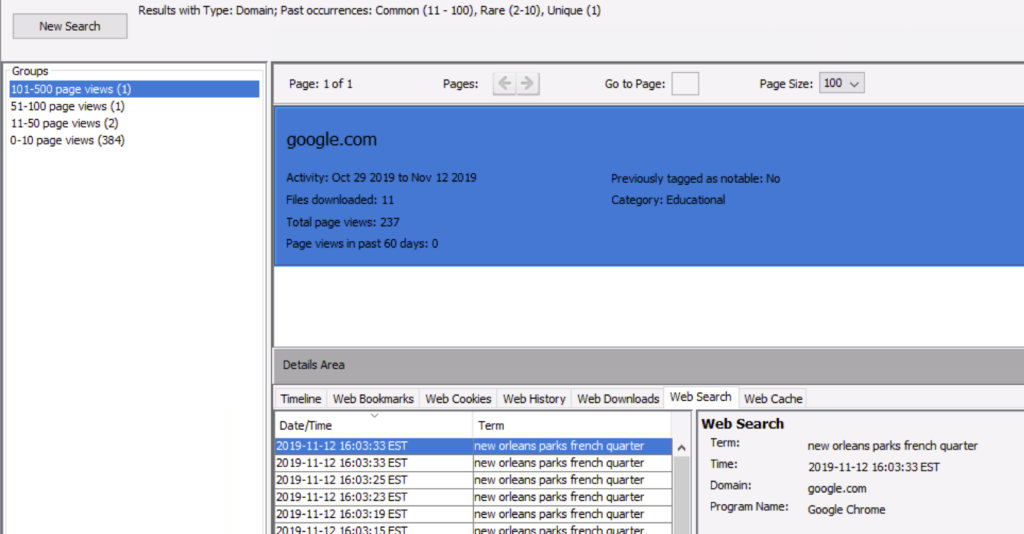
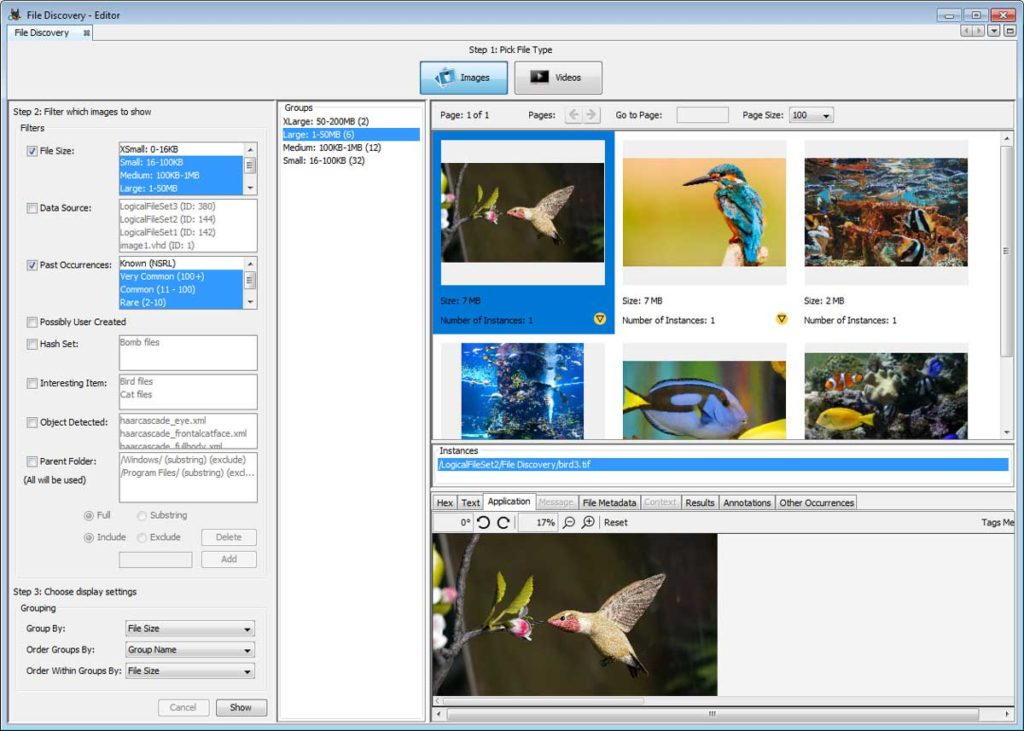
If you have a BitLocker encrypted drive, you can enter the recovery key when you add the drive and Autopsy (via The Sleuth Kit) will be able to decrypt it. This was added by the Cyber Triage team when the equivalent feature was there.
This feature is available only on Windows. If the drive is encrypted, but does not have a password, Autopsy will automatically decrypt it without the recovery key.
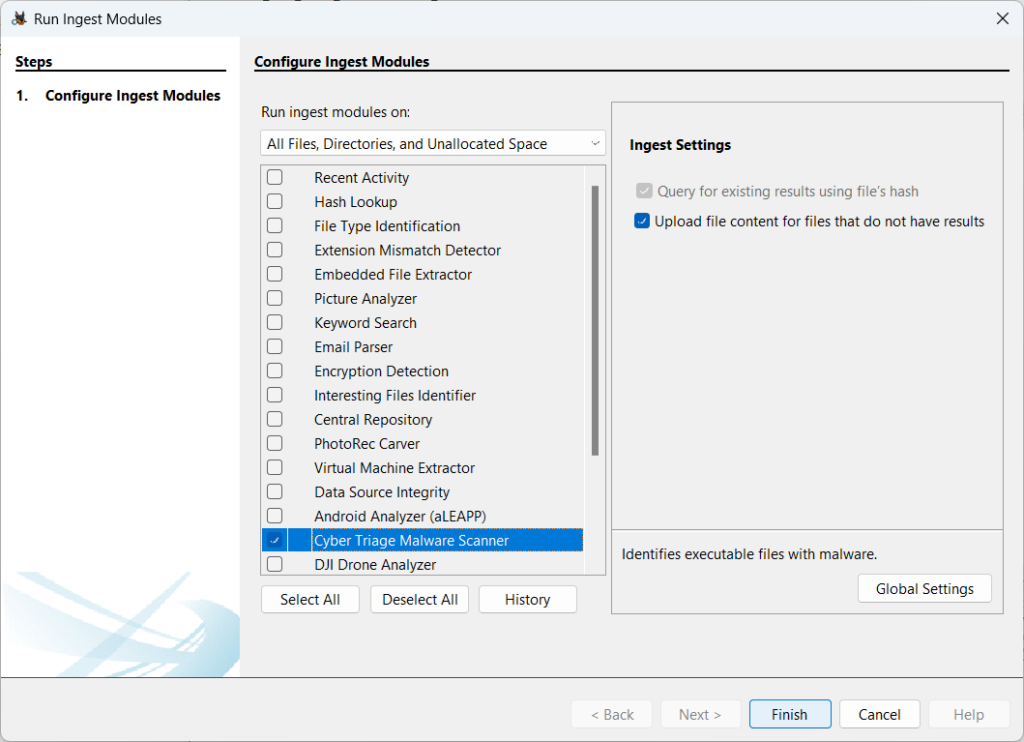
Run Alongside Cyber Triage
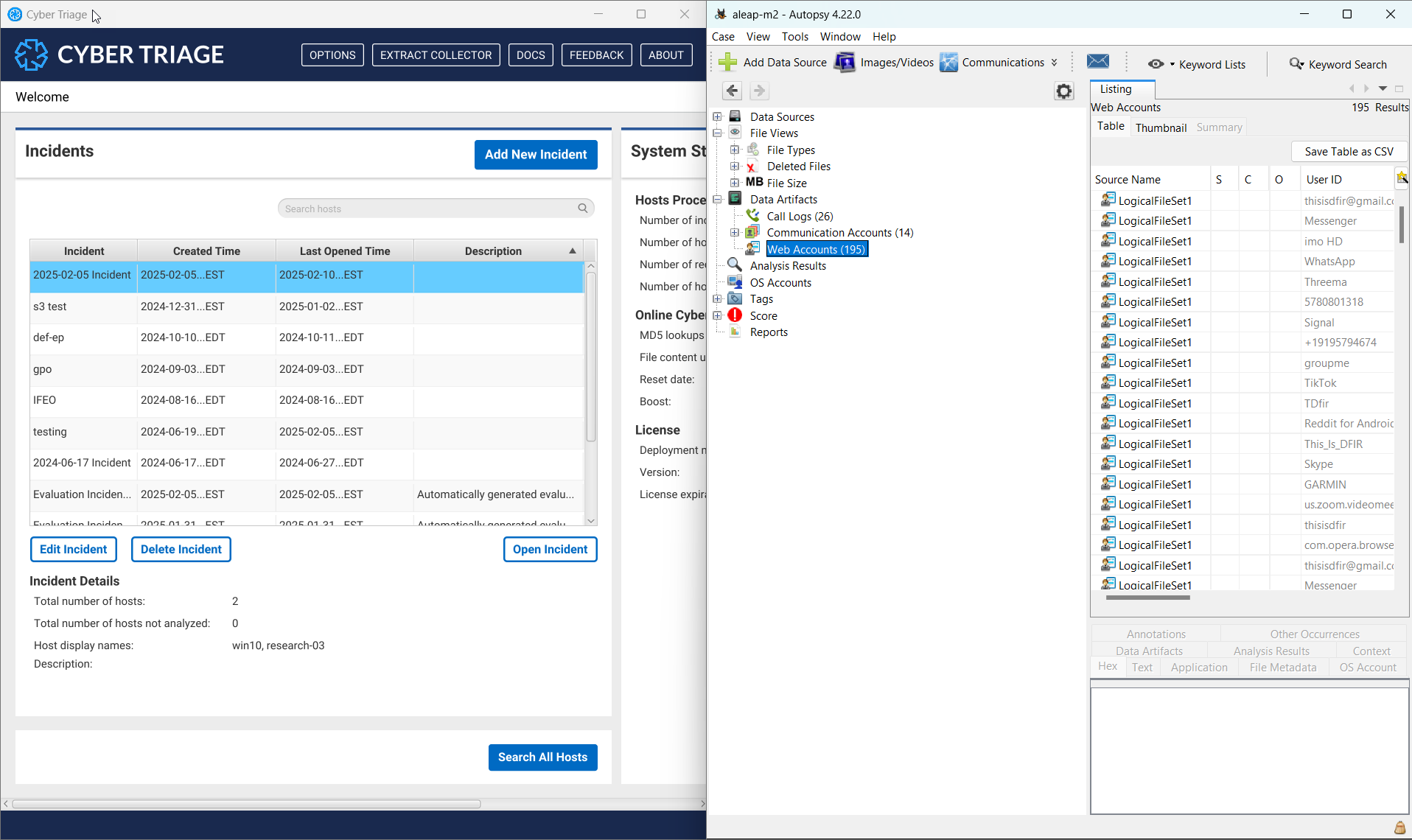
You can now run Autopsy and Cyber Triage at the same time. They historically had a file path conflict because they both use the same underlying Sleuth Kit library.
This scenario would come about when investigators would first use Cyber Triage to get a basic understanding of what happened on a host. If the investigator wanted to then perform a deeper dive on the host to perform carving or full text search, they would pivot to Autopsy.
Cyber Triage has an Autopsy export module to make it easy to go from one tool to the other, but you had to shut each application down to use the other.
Now you can have them open at the same time!
About Cyber Triage
Cyber Triage is built by the same engineers as Autopsy. It is focused on computer intrusions and remote access.
Use cases include:
- Corporate security team investigating a host after an EDR alert.
- Incident response teams investigating an entire network.
- Law enforcement looking for remote access on CSAM cases in response to Trojan Defense.
Cyber Triage has its own forensic collector easily deployed via EDRs and other agents. Its main benefit is the automated analysis that allows you to focus on a subset of artifacts instead of forcing you to review thousands.
You can get a free 7-day evaluation from here.
Intrusions Webinar with Brian Carrier
If you work in corporate security, Brian Carrier and Markus Schober are hosting a webinar on March 27th you might want to attend. It’s all about the attacker activity EDRs miss before the alert and how to find it.
They will cover:
- The attack life cycle.
- EDR evasion tactics.
- How attacks are detected.
- How to find pre-alert activity.
You can register here.
Download Autopsy
You can download the latest Autopsy from here.